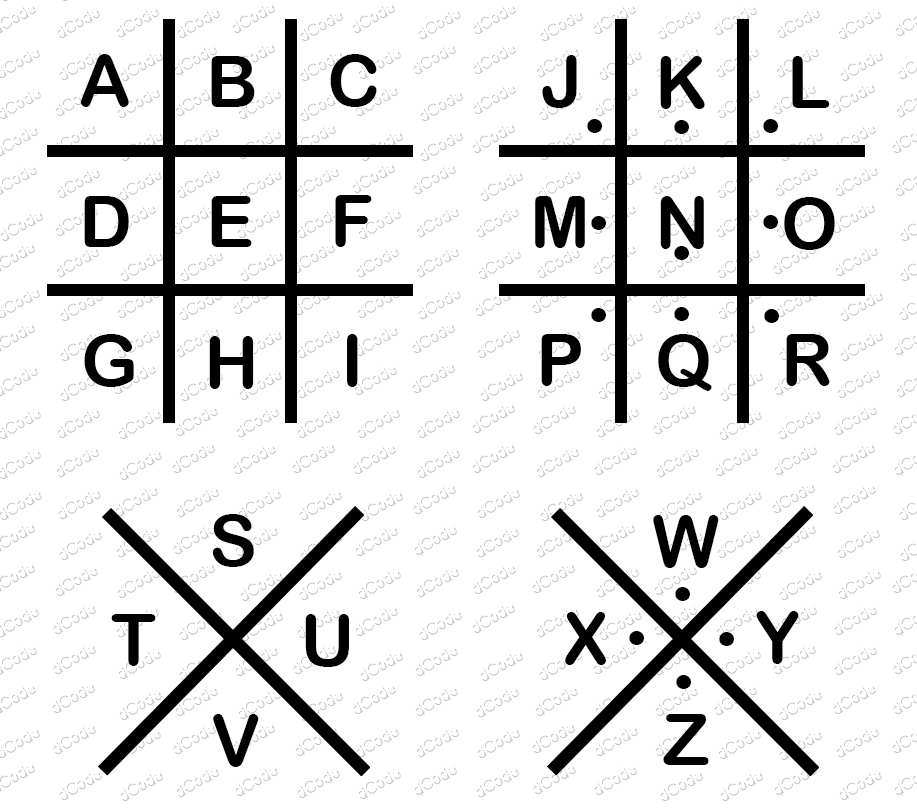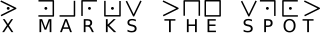Encryption of electronic communication signals use coding techniques so that no one other than the intended recipient can decode the message.
A. Read a book or several articles about the history and methods of encryption.
History of Encryption
– A Brief History of Encryption: This article explores the evolution of encryption from ancient times to modern-day cryptography.
– The History of Cryptography by IBM : A detailed look at how cryptography has developed over centuries, including its role in cybersecurity.
– History of Cryptography on Wikipedia A comprehensive overview of cryptographic methods and their historical significance.
Methods of Encryption
– 10 Common Encryption Methods : A guide to modern encryption techniques and their applications in cybersecurity.
– Data Encryption Methods & Types : A beginner-friendly explanation of encryption methods, including symmetric and asymmetric encryption.
– Types of Encryption : An in-depth discussion of encryption types, algorithms, and their significance.
B. Show an example code including encoding and decoding key(s).
Here’s and example of a Pigpen Cipher
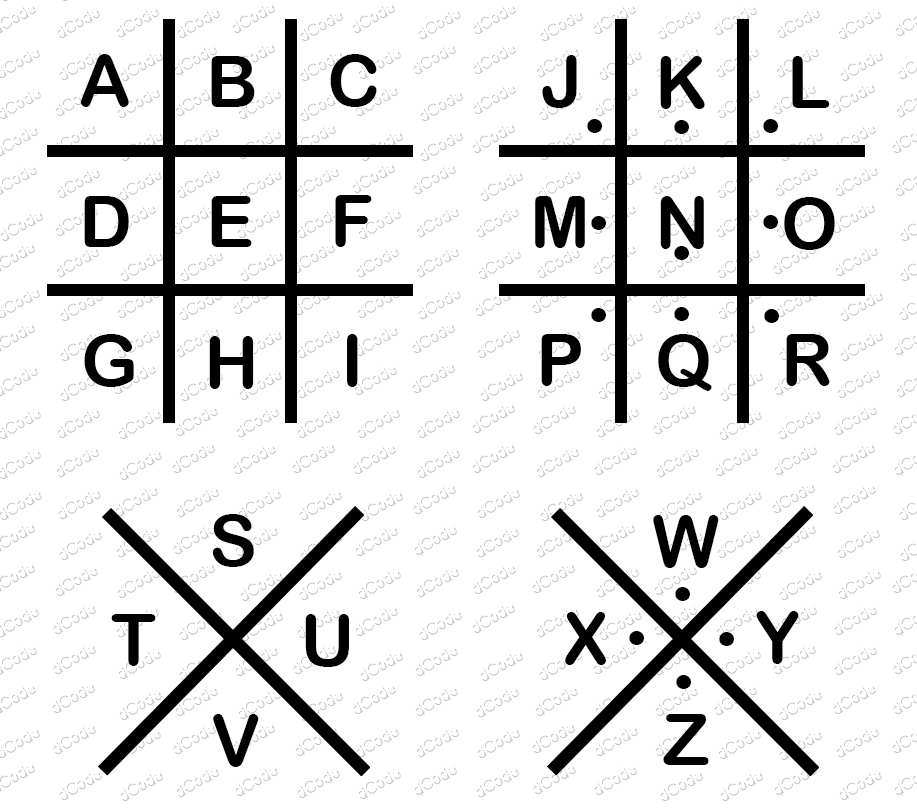
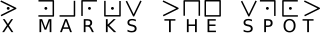
C. Demonstrate encoding and decoding messages with another person.
Use the above cipher and write a message!
D. Learn who the wartime “code talkers” were and how they used encrypted or secret communication.
The wartime “code talkers” were Native American soldiers who played a crucial role in secure military communications during World War I and World War II. They used their native languages to create unbreakable codes for transmitting sensitive information on the battlefield.
How They Operated:
1. Language as a Code: The code talkers used their indigenous languages, which were largely unwritten and unfamiliar to outsiders, as the foundation for their codes. For example, the Navajo language was famously used during World War II because of its complexity and lack of written form.
2. Code Development:
– In some cases, they developed formal codes based on their languages. For instance, the Navajo code included words for military terms that didn’t exist in their language. For example, “submarine” was translated as “iron fish.”
– They also used substitution ciphers, where words in their language represented letters or phrases in English.
3. Communication: Code talkers transmitted messages over radios and telephones. Their codes were so effective that they were never broken by enemy forces, even under intense scrutiny.
Historical Impact:
– The use of code talkers significantly improved the speed and security of military communications, contributing to key victories in battles such as Iwo Jima during World War II.
– Their contributions were recognized as a vital part of the Allied war effort, and they are celebrated for their ingenuity and bravery.
You can learn more about their incredible contributions here or here.
|